BREACH ALERT:
The news of the Microsoft Exchange Server hack is still developing. This cyberattack is still ongoing and the fight against it continues. In the past 24 hours, the team has observed “exploitation attempts on organizations doubling every two to three hours.” (zdnet.com, 2021) Due to the depth and size of the initial attack, it is taking time to completely recover, and patches are being released along the way. The ongoing issue is that hackers aren’t going to just sit around and wait for full recovery before they strike again. “Cyberattackers are taking full advantage of slow patch or mitigation processes on Microsoft Exchange Server with attack rates doubling every few hours.” (zdnet.com, 2021)
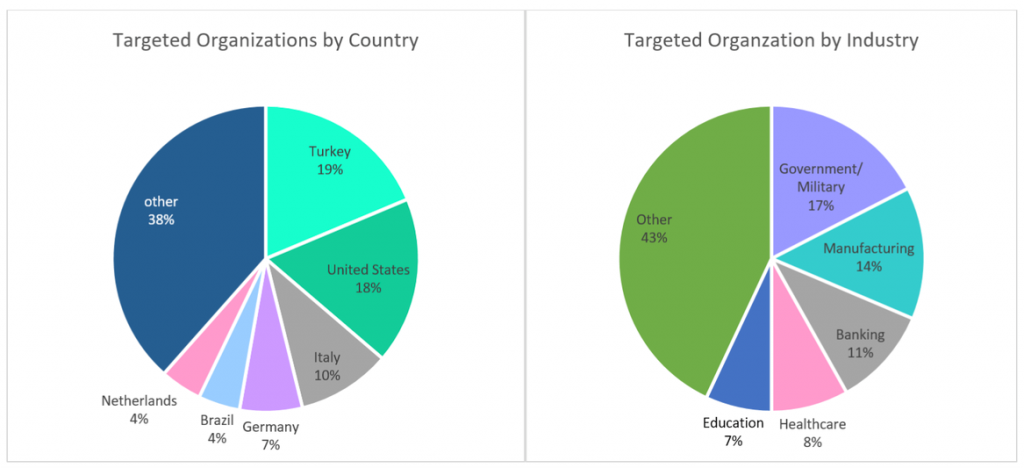
As noted by the chart above, you can see that the countries being hit the hardest are the United States, Turkey, and Italy, seeing 18%, 19%, and 10% of all attacks, respectfully. The attackers are not just spreading out across the globe, they are spread across industries as well. As you can imagine, based on the industries that are being impacted the hardest, these attacks are not being taken lightly. The repair and recovery are a work in progress. “Palo Alto estimates that at least 125,000 servers remain unpatched worldwide.” (zdnet.com, 2021)
Earlier this year, in January, a dangerous malware botnet named Emotet was disrupted by international law enforcement. Since then, a new malware has arrived to stand in the vacancy left by the previous botnet. Trickbot malware is causing aggravations and frustrations everywhere it is deployed. “Trickbot offers many of the same capabilities as Emotet, providing cybercriminals with a means of delivering additional malware onto compromised machines – and according to analysis of malware campaigns by cybersecurity researchers at Check Point, it’s now become the most commonly distributed malware in the world.” (zdnet.com, 2021)
HOW IT COULD AFFECT YOU:
Your onsite IT team and or your off-premise IT manager should have already scanned your systems and if you were exposed to the attack, they should have already implemented the patches. “Compromised servers could enable an unauthorized attacker to extract your corporate emails and execute malicious code inside your organization with high privileges,” commented Lotem Finkelstein, Manager of Threat Intelligence at Check Point. “Organizations who are at risk should not only take preventive actions on their Exchange, but also scan their networks for live threats and assess all assets.” (zdnet.com, 2021) If these steps to access, detect, and respond to these attacks have not already been taken with regards to your servers, you could still be swimming in open waters with hackers circling like sharks.
HODGSON CAN HELP:
Hodgson Consulting & Solutions specializes in securing data and information loss prevention for companies with multiple locations and/or a remote workforce. We monitor our clients’ systems 24/7 to ensure their systems and servers are in good standing. We offer full solutions for your IT needs, not just quick or Band-Aid fixes. Contact us to receive a FREE Dark Web Scan and also learn more about our Managed Security Service Plans. Call us today at 847-906-5005!



