Breach Alert
A facial recognition company, Clearview AI, released statements that someone gained unauthorized access to their entire customer list. As reported by the Daily Beast, the company has a database with over 3 million scraped images from the web and social media profiles, and they use that information to work with law enforcement agencies. (thedailybeast.com, 2020) With access to this many records, law enforcement agents won’t be the only ones who can do a quick search and potentially match your profile view with your profile image. According to the notification the company sent to its clients, “an intruder gained unauthorized access to its list of customers, to the number of user accounts those customers had set up, and to the number of searches its customers have conducted. The notification said the company’s servers were not breached and that there was no compromise of Clearview’s systems or network, and went on to say that they fixed the vulnerability and that the intruder did not obtain any law-enforcement agencies’ search histories.” (thedailybeast.com, 2020)
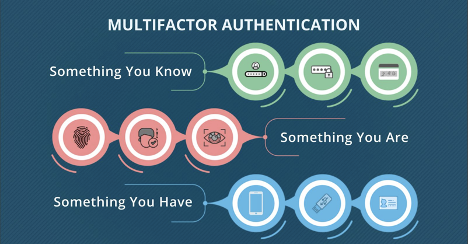
As if learning that your photos may now be in the hands of hackers isn’t enough, ZDNet recently reported that there is now android malware that can steal Google Authenticator 2FA codes. (zdnet.com, 2020) This means that two-factor authentication may not be enough! Google Authenticator 2FA is a mobile app that can be used as a two-factor authentication layer for several online accounts. “Google launched the Authenticator mobile app in 2010. The app works by generating six to eight-digits-long unique codes that users must enter in login forms while trying to access online accounts.”(zdnet.com, 2020) But, according to reports, “a new version of the Cerberus Android banking Trojan may be able to steal those one-time codes that generated by the Google app, and this will allow it to bypass 2FA-protected accounts.” (zdnet.com, 2020) IF this feature of the malware strain works as predicted/intended, it will place this banking trojan in an “elite category of malware strains.” (zdnet.com, 2020) That is certainly something to think about!
How it Could Affect You
We have all heard the saying, “you are what you eat”. Well, another saying we should become use to is “you are only as secure as the information you provide online.” What this means is, without proper security protections being in place, and without keeping those protections current, your online identity will only place hackers and cybercriminals steps closer to affecting your real-life livelihood. Be smart about the types and the amount of personal identifiable information you share. If it is not required, think about refraining from providing it. And always steer clear of providing information with unverified sites and sources. Stay two steps ahead of hackers by always staying up to date with your personal and professional security settings and system solutions.
Hodgson Can Help
While most people in the age of social media willingly share photos online via their different accounts, no one wants to think about those images potentially being “stolen”. Possibly more concerning than your images being hacked is the additional trails of information those images can lead hackers to. Here at Hodgson Consulting & Solutions, we specialize in securing data and information loss prevention for companies with multiple locations and/or a remote workforce. Contact us to receive a FREE 17- Point Confidential Technology Security Consultation and also learn more about our Managed Security Service Plans. Contact our office today at 847-906-5005.


